The Web lives in a sandbox. An important one. It means that you can click around on links and “feel” safe (that is, until you go to a talk by Jeremiah Grossman).
On your desktop however, you have a binary situation. You either run some code that can do pretty much anything (ignoring file permissions and virtualization etc) or you don’t run that code.
One of the dialogs that I dislike is from OS X when you “download something from the Internet”:
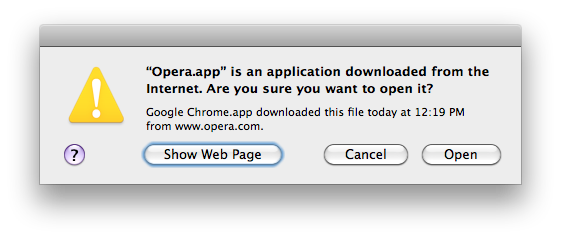
I would love to see the stats that Apple may have on how people react to this. I can imagine a scenario where something has mistakenly been downloaded and run, but I would guess that 99% of the time a user goes through the following:
- Click on something to download an app
- Run the app, because I wanted to, hence me clicking on it
- I have no information here…. so I think I will just click yes!
Some will yell, “think of the children!” and that if this popup has stopped ONE virus or malware through, it is worth the pain for the other millions of up pops.
Surely we can do better. Of all of the features in the IE9 beta, one that may not shout out as you as much as fancy fast chess or goldfish bowls, is how they manage this situation.
In Dean’s whirlwind keynote presentation (very nicely produced!) he showed a feature where clicking on a particular .exe wouldn’t alert the user based on crowd data. Basically, if enough people have used foo.exe and it is trusted, it can Just Get Through.
The virus scanning world is doing a lot of this on the backend. Places with scale can monitor the crowd and do a lot more than we have done now, and I can’t wait to see what comes of this.
We have talked about social permissions before. It will be great when I can see that Jeremiah Grossman is using a particular application for example ;) I look forward to a way out of app permissions hell.